
Apr 5, 2021 | Claim Status Inquiry, Claims, Denied Claims, RCM Insight
If a medical billing program has “scrubbing,” why did my medical billing claim still get denied? It is a common question that we are going to answer today.
First, let’s get a better understanding of the words we are talking about. In the medical billing world, validation and scrubbing tend to be used interchangeably. While they are similar – they are not actually the same. Understanding what you have and what you need will help you submit ‘clean’ claims.
According to Technopedia, data validation checks for the integrity and validity of data and ensures the data complies with the requirements. So, what requirements? Often people assume that this means payer requirements, but that is typically not standard. Validation rules are built into your practice management software and can be used for several points. Following are some common rules you may find in your program:
- Ensure NPI‘s and Tax IDs are the appropriate lengths
- Ensure patients date of birth is entered
- Ensure that a procedure code and place of service are present on each claim
While these scenarios are standard across the industry, there may be other situations that a validation rule can help. Some programs will allow you to create custom rules for your practice. A customized validation rule will allow you to create a rule for a payer requirement. For instance, you could create a rule to prevent the following:
- Do you have a code that always requires a modifier, but only for a specific payer?
- Work with pediatrics and always need the ‘relationship to insured’ to read something other than self
- How about insurance ID numbers that are a specific alpha-numeric combo, like 3 letters followed by 9 digits?
Keep in mind, if you are creating validation rules the program will make sure that the criteria are met based on the rule entered into your software. When creating custom rules, it is important to note that this will not verify payer billing guidelines. You will need to obtain information directly from your payer to create a rule that coincides with their policies.
Once any validation errors have been addressed your claims will go to the clearinghouse you are working with. Most clearinghouses offer claim scrubbing for an additional fee. Technopedia defines data scrubbing as the procedure of identifying and then modifying or removing incomplete, incorrect, inaccurately formatted, or repeated data.
Claim scrubbing is available in several ways. It may be used within your practice management system, your clearinghouse, or even a third-party vendor. Claim scrubbing services can vary greatly in what they are looking for.
Once the claim has left your practice management system it will likely go through at least 2 scrubbing programs—one with the clearinghouse and one with your payer, prior to accepting the claim for processing. When claims are found to have an error, these results are sent back through a Claim Status Report (ANSI 277 file or a human-readable text file). This report will include information about why the claim cannot be processed. This report will also indicate whether it is the clearinghouse or the payer that is rejecting the claim. If you have further questions about the rejection, you will need to contact the entity that has rejected it.
Checking the Claim Status Reports on a regular basis will help you correct the errors and resubmit in a timely manner. In addition, the information you have gathered from the rejections can be used to update internal processes or create customized validation rules to prevent future rejections for the same error–saving you time and money!
RCM Insight is a medical billing company that uses EZClaim’s medical billing software. For any details that have to do with claims validation and “scrubbing,” contact RCM Insight directly.
ABOUT EZCLAIM:
EZClaim is a medical billing and scheduling software company that provides a best-in-class product, with correspondingly exceptional service and support. Combined, they help improve medical billing revenues. To learn more, visit EZClaim’s website, e-mail them, or call them today at 877.650.0904.
[ Contribution by Stephanie Cremean’s with RCM Insights ]

Mar 10, 2021 | Cloud Security, HIPAA, Live Compliance, Medical Billing Software Blog
How Can You Avoid Phishing Scams?
Phishing is the fraudulent practice of sending e-mails or text messages claiming to be from reputable companies in order to persuade individuals to reveal personal information, such as passwords and credit card numbers. Scammers use e-mail or text messages to trick you into giving them your personal information, trying to steal your passwords, credit card account numbers, or Social Security numbers. If they get that information, they could gain access to your accounts. Scammers launch thousands of phishing attacks like these every day—and they are OFTEN successful!
The FBI Internet Crime Complaint Center reported that $57 million was lost to phishing schemes in one year. Scammers often update their tactics, but there are some signs that will help you recognize a phishing e-mail or text message.
How to Recognize Phishing Scams
First, phishing e-mails and text messages may look like they are from a company you know or trust. They may look like they are from a bank, a credit card company, a social networking site, an online payment website, or an app or online store. Phishing e-mails and text messages often tell a story to trick you into clicking on a link or opening an attachment.
They may:
- Say they have noticed some “suspicious activity or log-in attempts”
- Claim there is a problem with your account or your payment information
- Say you “must confirm some personal information”
- Include a fake invoice
- Want you to click on a link to make a payment
- Say you are “eligible to register for a government refund”
- Offer a coupon for free stuff
What are the Signs of a Scam?
- The e-mail says your account is “on hold because of a billing problem.“
- The e-mail has a generic greeting, “Hi Dear.” (If you have an account with the business, it probably would not use a generic greeting like this).
- The e-mail invites you to click on a link to “update your payment details.”
Your e-mail spam filters may keep many phishing e-mails out of your inbox, BUT scammers are always trying to outsmart the spam filters. So, it is a good idea to add extra layers of protection.
Four Steps You Can Take Today
- Protect your computer by using security software.
Set the software to update automatically so it can deal with any new security threats.
- Protect your mobile phone by setting software to update automatically. These updates could give you critical protection against security threats.
- Protect your accounts by using multi-factor authentication. Some accounts offer extra security by requiring two or more credentials to log in to your account.
- Protect your data by backing it up. You can copy your computer files to an external hard drive or cloud storage. Be sure to check with
your IT department and designated Security Officer before copying data to other locations.
What to Do If You Suspect a Phishing Attack?
If you get an e-mail or a text message that asks you to click on a link or open an attachment, first answer this question: Do I have an account with the company or know the person that contacted me?
- If the answer is “No,” it could be a phishing scam
- If the answer is “Yes,” contact the company directly using a phone number or website you know is real, NOT the information in the e-mail. Attachments and links can install harmful malware.
- If you think a scammer has your information, like your Social Security, credit card, or bank account number, go to IdentityTheft.gov. There you will see the specific steps to take based on the information that you lost.
- If you think you clicked on a link or opened an attachment that downloaded harmful software, update your computer’s security software. Then run a scan.
- Finally, contact your Security Officer and IT Staff Immediately.
What Can I Do to Ensure This Doesn’t Happen?
One of EZClaim’s partners, Live Compliance, will make checking off your compliance requirements extremely simple. They have a service that is:
- Completely online, our role-based courses make training easy for remote or in-office employees.
- Contact-free, accurate Security Risk Assessments are conducted remotely. All devices are thoroughly analyzed regardless of location. Conducting an accurate and thorough Security Risk Assessment is not only required but is a useful tool to expose potential vulnerabilities.
- Built directly into your portal, easily monitor where your workforce may be vulnerable with our Dark Web Breach Searches. Easily expose breach sources with ongoing searching of active employee email or domain ensuring continued awareness of potential breach exposure. Weekly automatic e-mail notifications if new breaches are discovered.
- Informational, and has short, informative, privacy awareness videos covering technical, administrative, and physical safeguards with topics such as Ransomware, Phishing, the Dark Web, Password Protection, etc. Delivered monthly with no logins required, empower your workforce to make conscious decisions when it comes to your organization’s privacy and security.
So, don’t risk your company’s future and avoid phishing scams especially when Life Compliance is offering a FREE Organization Assessment to help determine your company’s status. Call them at 980.999.1585, e-mail them at Jim@LiveCompliance.com, or visit LiveCompliance.com. For more specific information, e-mail support@livecompliance.com
ABOUT EZCLAIM:
EZClaim is a medical billing and scheduling software company that provides a best-in-class product, with correspondingly exceptional service and support. Combined, they help improve medical billing revenues. To learn more, visit EZClaim’s website, e-mail them, or call them today at 877.650.0904.
[ Article contributed by Jim Johnson of Live Compliance | Photo Credit: Shutterstock ]

Jan 11, 2021 | Administrative Safeguards, HIPAA, Live Compliance, Partner
The “Organizational Assessment“ is one simple step to avoid becoming a victim of dark web breaches.
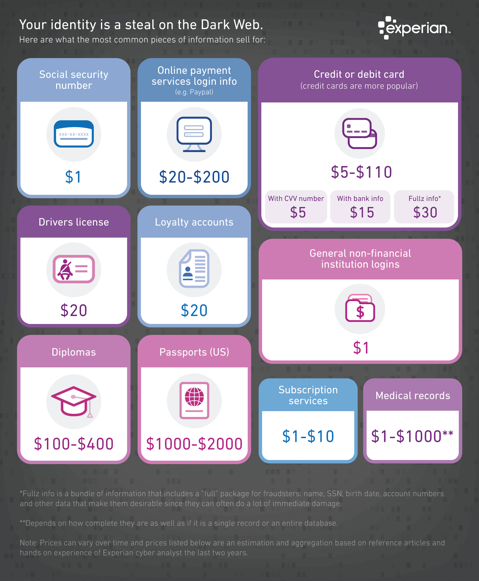
There’s no secret that the Dark Web is a scary place to lose your information. Medical records information sell anywhere from $1-$1000 by identity thieves! So, what if it affected your entire company?
What is a “breach” and where has the data come from?
A “breach” is an incident where data is inadvertently exposed in a vulnerable system, usually due to insufficient access controls or security weaknesses in the software. Data breaches are becoming more common and sometimes out of your control.
You can protect yourself and/or your organization by:
- Carefully monitoring where you store and enter your passwords can be extremely beneficial to help minimize the risk of a hack and keeping personal or patient information protected
- Routine password changes and monitoring where you store and enter your passwords can be extremely beneficial to help reduce the risk of becoming a victim to a hacker. Passwords should be long, unique in characters, capitalization, and alphanumerical
If you believe sensitive information about your organization was compromised, report it to the appropriate people within the organization, including network administrators, so they can be alert for any suspicious or unusual activity.
The web browser, Firefox, has a “Monitor” that will warn you by saying, “Your password is your first line of defense against hackers and unauthorized access to your accounts. The strength of your passwords directly impacts your online security.”
EZClaim’s partner, Live Compliance, can help. They aggregate breaches and enable you to assess where your personal data has been exposed. Dark Web scanning is built right into the Live Compliance portal, which allows a company to keep an eye on employees whose information was involved in a breach (and where the breach took place), and the suggested next steps to take.
What can I do to ensure this doesn’t happen to me or my organization?
Live Compliance can make checking off your compliance requirements extremely simple. It provides:
- Reliable and effective compliance
- Completely online, our role-based courses make training easy for remote or in-office employees
- Contact-free, accurate Security Risk Assessments are conducted remotely. All devices are thoroughly analyzed regardless of location. Conducting an accurate and thorough Security Risk Assessment is not only required, but is a useful tool to expose potential vulnerabilities, including those such as password protection.
- Policies and Procedures curated to fit your organization ensuring employees are updated on all Workstation Use and Security Safeguards in the office, or out of the office, all updated in real-time
- Electronic, prepared document sending and signing to employees and business associates
So, don’t risk your company’s future on dark web breaches. Contact one of EZClaim’s partners, Live Compliance, especially since they are offering a FREE Organization Assessment to help determine your company’s status. E-mail them, visit their website at LiveCompliance.com , or call them at 980.999.1585.
For more information about EZClaim’s medical billing software, e-mail, visit their website, or contact them at 877.650.0904.
[ Article contributed by Jim Johnson of Live Compliance ]

Dec 14, 2020 | Live Compliance, Medical Billing Software Blog, Partner, Support and Training
There are a few HIPAA items to focus on RIGHT NOW—before the end of 2020!
The U.S. Department of Health and Human Services (HHS) has designated the “Health Insurance Portability and Accountability Act” (HIPAA) as the national standard for protecting the privacy and security of health information (in 1996). This led to the Health Information Technology for Economic and Clinical Health Act (HITECH), which has a provision in it for audits, and the HHS Office for Civil Rights is responsible for carrying out HIPAA audits, and responding to complaints and breaches. Ignoring them is not an option!
A Risk Assessment IS NOT Enough
A risk assessment is only one element of the compliance process. You must also “implement security updates as necessary and correct identified security deficiencies.” In other words, you must act via a Corrective Action Plan (CAP) and follow the required risk assessment process.
Dark Web
It is no secret that the “Dark Web” is a scary place to lose your information. So, what if it did happen and affected your entire company? Identity thieves get anywhere from $1-$1,000 for medical records, for each instance! So, how can you protect yourself and/or your organization?
Well, data breaches are becoming more common—sometimes which are out of your control—so carefully monitoring where you store and enter your passwords can be extremely beneficial to help minimize the risk of a hack and keeping personal or patient information protected.
One solution for this is the automatic Dark Web monitoring built into the portal of one of EZClaim’s partners, Live Compliance. Their solution helps keep an ‘eye’ on employees whose information was involved in a breach, and suggests next steps to take where the breach was found. Then, it allows your to conduct an accurate and thorough Security Risk Assessment. This is not only required, but is a useful tool to expose potential vulnerabilities, including those that involve password protection.
 So, what can I do to ensure this doesn’t happen to me or my organization? Well, Live Compliance makes checking off your compliance requirements extremely simple by providing:
So, what can I do to ensure this doesn’t happen to me or my organization? Well, Live Compliance makes checking off your compliance requirements extremely simple by providing:
● Reliable and effective compliance
● Completely online, our role-based courses make training easy for remote or in-office employees
● Contact-free, accurate Security Risk Assessments are conducted remotely. All devices are thoroughly analyzed regardless of location.
● Policies and procedures are curated to fit your organization, ensuring employees are updated on all workstation use and security safeguards in the office, or out. It is updated in real time.
● An electronic document is sent to employees and business associates
So, don’t risk your company’s future, especially when Live Compliance offers a FREE Organization Assessment to help determine your company’s status.
For additional details, call them at 980.999.1585, e-mail them, or visit their website at LiveCompliance.com
[ Article provided by Jim Johnson of Live Compliance ].
ABOUT EZCLAIM:
EZClaim is a medical billing and scheduling software company that provides a best-in-class product, with correspondingly exceptional service and support. Combined, they help improve medical billing revenues. To learn more, visit EZClaim’s website, e-mail them, or call a representative today at 877.650.0904.

Oct 12, 2020 | Medical Billing Software Blog, Partner, Revenue, Waystar
Today’s healthcare landscape faces truly unprecedented challenges, which means it’s more important to get the most out of your analytics to develop more informed, strategic decisions. There’s a deep well of data that each revenue cycle feeds into, which if properly analyzed, can help organizations operate at their most efficient and effective. Here are the four stages of data analytics workflows that are key to developing those actionable insights: A “Trigger,” or the point in your revenue cycle that sets up the call for deeper analysis; “Interpretation” of data to determine root causes and identify appropriate next steps; “Intervention” to improve specific metrics; and “Tracking” of said metrics to chart success in achieving desired outcomes.
So, let’s examine what a successful version of each stage looks like:
Trigger:
The trigger occurs when you notice something that needs further investigation. With the right analytics tool you can easily access all of your key performance indicators, financial goals and more, providing the visibility you need into your rev cycle. When something looks amiss or needs improving, you can drill down to the level that shows what’s really going on.
Interpretation:
Even a wealth of data amounts to nothing without an efficient way to process and communicate key takeaways. You’ll need to equip your team with access to concise reports, smart visualizations and relevant historical data in order to get them to the insights that drive action.
Intervention:
Now is the time to take action. Intervention is ultimately tied directly to your ability to drill down into the data underlying problematic areas of your revenue cycle and clearly communicate takeaways with your team. Success at this stage depends on designing a plan based on your best understanding of underlying issues and the most effective way to address them.
Tracking:
Your intervention plan is built on KPIs that naturally intertwine with the way you measure success across your revenue cycle. With proper implementation and tracking, running with the analytics cycle can become a simple addition to your everyday workflow. More than delivering on your initial goals, the true power of analytics is the ability to deliver repeat value on your initial investment.
Wrap Up
A strong analytics solution does more than deliver a more fully developed picture of your revenue cycle performance. It provides actionable business intelligence, cuts down on time between analysis and action, and lessens the strain on your IT department.
Waystar is a ‘partner’ of EZClaim, and provides analytics for a practice using their medical billing software. For more details about EZClaim’s products and services, visit their website: https://ezclaim.com/
To learn more about how Waystar can help you harness the power of your data, call their main office at 844-4WAYSTAR, or call sales at 844-6WAYSTAR.
[ Contributed by Waystar ]







