
Jul 12, 2022 | Live Compliance, Partner
Whether you’re a one-person billing company or a multi-location organization, it’s possible that you’ve seen or heard of Malware and the potential risks associated with it and how it can cause major downtime and potential HIPAA violations due to breached information.
Criminals use malware to steal personal information, send spam, and commit fraud. Malware includes viruses, spyware, and other unwanted software that gets installed on your computer or mobile device without your consent. These programs can cause your device to crash and can be used to monitor and control your online activity. They also can make your computer vulnerable to viruses and deliver unwanted or inappropriate ads.
Here are a few, high-level quick steps you can take to spot and avoid Malware.
First, let’s talk security software.
Install and update security software, and use a firewall. Set your security software, internet browser, and operating system (like Windows or Mac OS X) to update automatically, and don’t forget to Back up your data regularly. Strong security software can prevent a hack or scam before it happens. You should install well-known software directly from the source. Sites that offer lots of different browsers, PDF readers, and other popular software for free are more likely to include malware. Read each screen when installing new software. If you don’t recognize a program or are prompted to install additional “bundled” software, decline the additional program or exit the installation process.
Don’t change your browser’s security settings and pay attention to your browser’s security warnings. Many browsers come with built-in security scanners that warn you before you visit an infected webpage or download a malicious file.
Next, watch what you’re clicking on.
Instead of clicking on a link in an email, type the URL of a trusted site directly into your browser. Scammers send emails that appear to be from companies you know and trust. The links may look legitimate, but clicking on them could download malware or send you to a scam site. Don’t open attachments in emails unless you know who sent it and what it is. Opening the wrong attachment — even if it seems to be from friends or family — can install malware on your computer.
Avoid clicking on pop-ups or banner ads about your computer’s performance! Scammers insert unwanted software into banner ads that look legitimate, especially ads about your computer’s health. Avoid clicking on these ads if you don’t know the source.
Your computer may be infected with malware if it:
-
- slows down, crashes or displays repeated error messages
- won’t shut down or restart
- serves a multitude of pop-ups
- serves inappropriate ads or ads that interfere with page content
- won’t let you remove unwanted software
- injects ads in places you typically wouldn’t see them, such as government websites
- displays web pages you didn’t intend to visit, or sends emails you didn’t write
Other warning signs of malware include:
-
- new and unexpected toolbars or icons in your browser or on your desktop
- unexpected changes in your browser, like using a new default search engine or displaying new tabs you didn’t open
- a sudden or repeated change in your computer’s internet home page
- a laptop battery that drains quicker than it should
At Live Compliance, we make checking off your compliance requirements extremely simple.
- Reliable and Effective Compliance
- Completely online, our role-based courses make training easy for remote or in-office employees.
- Contact-free, accurate Security Risk Assessments are conducted remotely. All devices are thoroughly analyzed regardless of location. Conducting an accurate and thorough Security Risk Assessment is not only required but is a useful tool to expose potential vulnerabilities, including those such as Password Protection.
- Policies and Procedures curated to fit your organization ensuring employees are updated on all Workstation Use and Security Safeguards in the office, or out. Update in real-time.
- Electronic, prepared document sending and signing to employees and business associates.
Don’t risk your company’s future, especially when we are offering a free Organization Assessment to help determine your company’s status. Call us at (980) 999-1585, or email me, Jim Johnson at Jim@LiveCompliance.com or visit www.LiveCompliance.com
For more information about DarkWeb breaches please contact us at (980) 999-1585 or email us at support@livecompliance.com

Mar 10, 2021 | Cloud Security, HIPAA, Live Compliance, Medical Billing Software Blog
How Can You Avoid Phishing Scams?
Phishing is the fraudulent practice of sending e-mails or text messages claiming to be from reputable companies in order to persuade individuals to reveal personal information, such as passwords and credit card numbers. Scammers use e-mail or text messages to trick you into giving them your personal information, trying to steal your passwords, credit card account numbers, or Social Security numbers. If they get that information, they could gain access to your accounts. Scammers launch thousands of phishing attacks like these every day—and they are OFTEN successful!
The FBI Internet Crime Complaint Center reported that $57 million was lost to phishing schemes in one year. Scammers often update their tactics, but there are some signs that will help you recognize a phishing e-mail or text message.
How to Recognize Phishing Scams
First, phishing e-mails and text messages may look like they are from a company you know or trust. They may look like they are from a bank, a credit card company, a social networking site, an online payment website, or an app or online store. Phishing e-mails and text messages often tell a story to trick you into clicking on a link or opening an attachment.
They may:
- Say they have noticed some “suspicious activity or log-in attempts”
- Claim there is a problem with your account or your payment information
- Say you “must confirm some personal information”
- Include a fake invoice
- Want you to click on a link to make a payment
- Say you are “eligible to register for a government refund”
- Offer a coupon for free stuff
What are the Signs of a Scam?
- The e-mail says your account is “on hold because of a billing problem.“
- The e-mail has a generic greeting, “Hi Dear.” (If you have an account with the business, it probably would not use a generic greeting like this).
- The e-mail invites you to click on a link to “update your payment details.”
Your e-mail spam filters may keep many phishing e-mails out of your inbox, BUT scammers are always trying to outsmart the spam filters. So, it is a good idea to add extra layers of protection.
Four Steps You Can Take Today
- Protect your computer by using security software.
Set the software to update automatically so it can deal with any new security threats.
- Protect your mobile phone by setting software to update automatically. These updates could give you critical protection against security threats.
- Protect your accounts by using multi-factor authentication. Some accounts offer extra security by requiring two or more credentials to log in to your account.
- Protect your data by backing it up. You can copy your computer files to an external hard drive or cloud storage. Be sure to check with
your IT department and designated Security Officer before copying data to other locations.
What to Do If You Suspect a Phishing Attack?
If you get an e-mail or a text message that asks you to click on a link or open an attachment, first answer this question: Do I have an account with the company or know the person that contacted me?
- If the answer is “No,” it could be a phishing scam
- If the answer is “Yes,” contact the company directly using a phone number or website you know is real, NOT the information in the e-mail. Attachments and links can install harmful malware.
- If you think a scammer has your information, like your Social Security, credit card, or bank account number, go to IdentityTheft.gov. There you will see the specific steps to take based on the information that you lost.
- If you think you clicked on a link or opened an attachment that downloaded harmful software, update your computer’s security software. Then run a scan.
- Finally, contact your Security Officer and IT Staff Immediately.
What Can I Do to Ensure This Doesn’t Happen?
One of EZClaim’s partners, Live Compliance, will make checking off your compliance requirements extremely simple. They have a service that is:
- Completely online, our role-based courses make training easy for remote or in-office employees.
- Contact-free, accurate Security Risk Assessments are conducted remotely. All devices are thoroughly analyzed regardless of location. Conducting an accurate and thorough Security Risk Assessment is not only required but is a useful tool to expose potential vulnerabilities.
- Built directly into your portal, easily monitor where your workforce may be vulnerable with our Dark Web Breach Searches. Easily expose breach sources with ongoing searching of active employee email or domain ensuring continued awareness of potential breach exposure. Weekly automatic e-mail notifications if new breaches are discovered.
- Informational, and has short, informative, privacy awareness videos covering technical, administrative, and physical safeguards with topics such as Ransomware, Phishing, the Dark Web, Password Protection, etc. Delivered monthly with no logins required, empower your workforce to make conscious decisions when it comes to your organization’s privacy and security.
So, don’t risk your company’s future and avoid phishing scams especially when Life Compliance is offering a FREE Organization Assessment to help determine your company’s status. Call them at 980.999.1585, e-mail them at Jim@LiveCompliance.com, or visit LiveCompliance.com. For more specific information, e-mail support@livecompliance.com
ABOUT EZCLAIM:
EZClaim is a medical billing and scheduling software company that provides a best-in-class product, with correspondingly exceptional service and support. Combined, they help improve medical billing revenues. To learn more, visit EZClaim’s website, e-mail them, or call them today at 877.650.0904.
[ Article contributed by Jim Johnson of Live Compliance | Photo Credit: Shutterstock ]

Feb 9, 2021 | Administrative Safeguards, Cloud Security, Live Compliance, Medical Billing Software Blog, Partner
Ransomware hackers target medical billing companies, and it CAN AFFECT your entire company! (Ransomware is a type of malicious software designed to block access to a computer system until a sum of money is paid.)
Often out of one’s control, ransomware hackers target medical billing companies because of the tremendous value of the data. BUT, there are steps that CAN BE TAKEN to protect you, your company, and your patients and/or clients.
NetWalker Ransomware, for example, gained notoriety for targeting hospitals and healthcare providers with e-mails claiming to provide information about COVID-19. (The e-mail usually has an attachment that downloads the ransomware from a remote server when clicked on.) The thing is, this is very lucrative for identity thieves since medical records information sells anywhere from $1-$1000!
As the number of healthcare providers taking advantage of Telehealth continues to increase—now outnumbering in-person visits—the number of ransomware attacks continues to increase as well. This means Billers and Providers must be aware of the programs that are used on their machines and ensure necessary steps are taken to safeguard against hackers and attacks.
How can you protect yourself and/or your organization?
- Carefully monitoring where you store and enter your passwords can be extremely beneficial to help minimize the risk of a hack and keeping personal or patient information protected.
- Routine password changes and monitoring where you store and enter your passwords can be extremely beneficial to help reduce the risk of becoming a victim to a hacker. Passwords should be long, unique in characters, capitalization, and alphanumerical.
- Have you had an accurate and thorough Security Risk Assessment and/or penetration testing? If you haven’t completed an accurate and thorough security risk assessment, you could also be penalized under ‘willful neglect’ (this category alone is $50,000 per violation!) in addition to the higher risk of ransomware attacks.
- If you believe you might have revealed sensitive information about your organization, report it to the appropriate people within the organization, including network administrators. They can be alert for any suspicious or unusual activity.
- The strength of your passwords directly impacts your online security.
Live Compliance can help. They aggregate breaches which enables you to assess where personal data has been exposed. Dark Web scanning is built right into their Portal, and it allows you to keep an eye on employees whose information was involved in a breach, where the breach took place, and then suggest the next steps to take.
At Live Compliance, they make checking off your compliance requirements extremely simple and to ensure this doesn’t happen to you or your organization:
- Reliable and effective compliance
- Completely online, our role-based courses make training easy for remote or in-office employees
- Contact-free, accurate Security Risk Assessments are conducted remotely. All devices are thoroughly analyzed regardless of location. (Conducting an accurate and thorough Security Risk Assessment is not only required but is a useful tool to expose potential vulnerabilities, including those such as password protection.)
- Policies and procedures curated to fit your organization ensuring employees are updated on all workstation use and security safeguards in the office, or out of the office—all updated in real-time
- Electronic, prepared document sending and signing to employees and business associates
So, don’t risk your company’s future on ransomware hackers. Contact one of EZClaim’s partners, Live Compliance, especially since they are offering a FREE Organization Assessment to help determine your company’s status. E-mail them, visit their website at LiveCompliance.com, or call them at 980.999.1585.
For more information about EZClaim’s medical billing software, which provides a best-in-class product with correspondingly exceptional service and support, e-mail, visit their website, or contact them at 877.650.0904.
[ Article contributed by Jim Johnson of Live Compliance ]

Jan 11, 2021 | Administrative Safeguards, HIPAA, Live Compliance, Partner
The “Organizational Assessment“ is one simple step to avoid becoming a victim of dark web breaches.
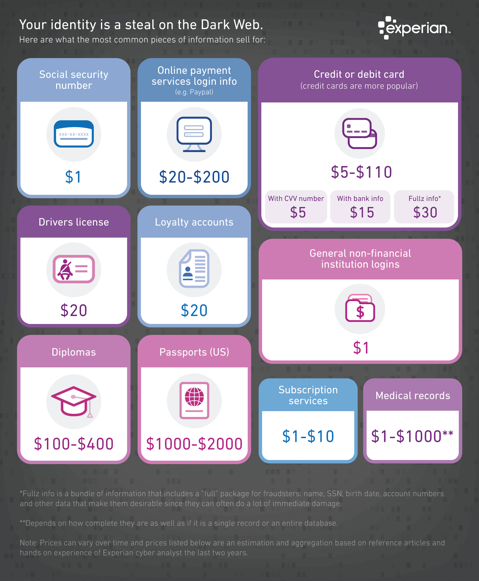
There’s no secret that the Dark Web is a scary place to lose your information. Medical records information sell anywhere from $1-$1000 by identity thieves! So, what if it affected your entire company?
What is a “breach” and where has the data come from?
A “breach” is an incident where data is inadvertently exposed in a vulnerable system, usually due to insufficient access controls or security weaknesses in the software. Data breaches are becoming more common and sometimes out of your control.
You can protect yourself and/or your organization by:
- Carefully monitoring where you store and enter your passwords can be extremely beneficial to help minimize the risk of a hack and keeping personal or patient information protected
- Routine password changes and monitoring where you store and enter your passwords can be extremely beneficial to help reduce the risk of becoming a victim to a hacker. Passwords should be long, unique in characters, capitalization, and alphanumerical
If you believe sensitive information about your organization was compromised, report it to the appropriate people within the organization, including network administrators, so they can be alert for any suspicious or unusual activity.
The web browser, Firefox, has a “Monitor” that will warn you by saying, “Your password is your first line of defense against hackers and unauthorized access to your accounts. The strength of your passwords directly impacts your online security.”
EZClaim’s partner, Live Compliance, can help. They aggregate breaches and enable you to assess where your personal data has been exposed. Dark Web scanning is built right into the Live Compliance portal, which allows a company to keep an eye on employees whose information was involved in a breach (and where the breach took place), and the suggested next steps to take.
What can I do to ensure this doesn’t happen to me or my organization?
Live Compliance can make checking off your compliance requirements extremely simple. It provides:
- Reliable and effective compliance
- Completely online, our role-based courses make training easy for remote or in-office employees
- Contact-free, accurate Security Risk Assessments are conducted remotely. All devices are thoroughly analyzed regardless of location. Conducting an accurate and thorough Security Risk Assessment is not only required, but is a useful tool to expose potential vulnerabilities, including those such as password protection.
- Policies and Procedures curated to fit your organization ensuring employees are updated on all Workstation Use and Security Safeguards in the office, or out of the office, all updated in real-time
- Electronic, prepared document sending and signing to employees and business associates
So, don’t risk your company’s future on dark web breaches. Contact one of EZClaim’s partners, Live Compliance, especially since they are offering a FREE Organization Assessment to help determine your company’s status. E-mail them, visit their website at LiveCompliance.com , or call them at 980.999.1585.
For more information about EZClaim’s medical billing software, e-mail, visit their website, or contact them at 877.650.0904.
[ Article contributed by Jim Johnson of Live Compliance ]

Dec 14, 2020 | Live Compliance, Medical Billing Software Blog, Partner, Support and Training
There are a few HIPAA items to focus on RIGHT NOW—before the end of 2020!
The U.S. Department of Health and Human Services (HHS) has designated the “Health Insurance Portability and Accountability Act” (HIPAA) as the national standard for protecting the privacy and security of health information (in 1996). This led to the Health Information Technology for Economic and Clinical Health Act (HITECH), which has a provision in it for audits, and the HHS Office for Civil Rights is responsible for carrying out HIPAA audits, and responding to complaints and breaches. Ignoring them is not an option!
A Risk Assessment IS NOT Enough
A risk assessment is only one element of the compliance process. You must also “implement security updates as necessary and correct identified security deficiencies.” In other words, you must act via a Corrective Action Plan (CAP) and follow the required risk assessment process.
Dark Web
It is no secret that the “Dark Web” is a scary place to lose your information. So, what if it did happen and affected your entire company? Identity thieves get anywhere from $1-$1,000 for medical records, for each instance! So, how can you protect yourself and/or your organization?
Well, data breaches are becoming more common—sometimes which are out of your control—so carefully monitoring where you store and enter your passwords can be extremely beneficial to help minimize the risk of a hack and keeping personal or patient information protected.
One solution for this is the automatic Dark Web monitoring built into the portal of one of EZClaim’s partners, Live Compliance. Their solution helps keep an ‘eye’ on employees whose information was involved in a breach, and suggests next steps to take where the breach was found. Then, it allows your to conduct an accurate and thorough Security Risk Assessment. This is not only required, but is a useful tool to expose potential vulnerabilities, including those that involve password protection.
 So, what can I do to ensure this doesn’t happen to me or my organization? Well, Live Compliance makes checking off your compliance requirements extremely simple by providing:
So, what can I do to ensure this doesn’t happen to me or my organization? Well, Live Compliance makes checking off your compliance requirements extremely simple by providing:
● Reliable and effective compliance
● Completely online, our role-based courses make training easy for remote or in-office employees
● Contact-free, accurate Security Risk Assessments are conducted remotely. All devices are thoroughly analyzed regardless of location.
● Policies and procedures are curated to fit your organization, ensuring employees are updated on all workstation use and security safeguards in the office, or out. It is updated in real time.
● An electronic document is sent to employees and business associates
So, don’t risk your company’s future, especially when Live Compliance offers a FREE Organization Assessment to help determine your company’s status.
For additional details, call them at 980.999.1585, e-mail them, or visit their website at LiveCompliance.com
[ Article provided by Jim Johnson of Live Compliance ].
ABOUT EZCLAIM:
EZClaim is a medical billing and scheduling software company that provides a best-in-class product, with correspondingly exceptional service and support. Combined, they help improve medical billing revenues. To learn more, visit EZClaim’s website, e-mail them, or call a representative today at 877.650.0904.







